Massive Cyber Attack and What You Need to Know
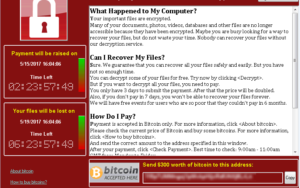
On Friday, May 12, 2017, the world was alarmed to discover that Cyber Crime had achieved a new record. In a widespread ransomware attack that hit organizations in more than 100 countries within the span of 48 hours, the operators of malware known as WannaCry/WanaCrypt0r 2.0 are believed to have caused the biggest attack of its kind ever recorded.
What is WannaCry?
WannaCry, WanaCrypt, or Wcry for short, is ransomware that works like other malware of its type, with a few intricacies that highlight the sophistication of its operators.
Malware spreads like a worm, crawling from one computer to all other devices connected to it. This particular malware comes with an encryption package attached to it which automatically downloads itself locking up all data and demands a ransom. WannaCry deletes all copies, disables Windows startup recovery, and clears the Windows Server Backup history to prevent victims from restoring their files without paying the ransom. All it takes is one computer to be infected to shut down and an entire network within your organization.
Perhaps more than anything else, this ransomware onslaught is a resounding reminder of security basics, especially when it comes to Microsoft product patching. Those who applied critical Microsoft Windows patches released in March were protected against this attack.
In addressing whether ransomware attacks are generally considered reportable breaches, “Under HIPAA, a breach is defined as the acquisition, access, use or disclosure of PHI in a manner not permitted under the HIPAA Privacy Rule which compromises the security or privacy of the PHI”. In a significant statement that aims to clarify reporting requirements, the guidance also points out: “When electronic PHI is encrypted as the result of a ransomware attack, a breach has occurred because the ePHI encrypted by the ransomware was acquired by unauthorized individuals [who] have taken possession or control of the information, and thus is a ‘disclosure’ not permitted under the HIPAA Privacy Rule”.
Fortunately, existing Cytek clients can rest easy. We have been preparing for such an attack for quite some time now and we have already taken proactive majors to protect your organization by applying security patches and installing different Threat Intelligence tools on your server!
As a company who researches infections, exploitations and various other information security related items, knowing is half the battle. Especially when items are being leaked and created in this kind of rapid-fire fashion. There has been A LOT of detections of these objects recently, our dashboard lit up like a Christmas tree within the last few weeks/months and we do not expect it to stop anytime soon. We are dedicated to protecting you and your business as we work around the clock to achieve this goal. Please educate your employees about what’s going on and be sure they are up to speed and are extra careful on what websites and emails they open and what they are clicking on!
Our team has warned of these threats in several of our blogs before today. This is only the beginning; new versions have been recoded over the weekend in order to bypass patches that have been made. Please take the security of your organization seriously and take proactive steps to protect your customer’s data today!
If you have any questions or for immediate assistance feel free to call our emergency line at
844-644-8744.
Not a current client? Contact our office today for detailed instructions to protect you and your organization against such an attack.

 ">
">
 ">
">